In the digital realm, Email Authentication for Better Deliverability stands as a pivotal element in safeguarding communication integrity. This guide delves into the nuanced layers of email authentication, unraveling how SPF, DKIM, and DMARC not only fortify your email security but also reshape the dynamics of digital correspondence. Embark on this journey to understand the intricate mechanics and strategic applications that make email authentication a cornerstone of modern digital communication.
| Aspect | Detail |
|---|---|
| Focus | Email Authentication for Better Deliverability |
| Protocols | SPF, DKIM, DMARC |
| Benefits | Improves sender reputation, reduces bounce rates, boosts email engagement |
| Security | Includes TLS Encryption, use of Dedicated IP Addresses |
| Goal | Securing email channels, ensuring successful delivery |
Table of Contents
SPF Explained for Better Email Authentication and Deliverability
Concept and Mechanism
SPF stands as a cornerstone in Email Authentication for Better Deliverability. At its core, SPF is a protocol designed to authenticate outbound emails, ensuring they originate from authorized servers. This mechanism helps in identifying and blocking spam and phishing attempts, thereby safeguarding the sender’s reputation.
Implementation Guide
Implementing SPF involves a few straightforward steps:
- Identify sending domains: List all domains used to send emails.
- Create an SPF record: This DNS record outlines authorized sending IPs.
- Publish the record: Update your DNS settings with the SPF record.
- Test: Utilize tools like MXToolBox to verify your SPF record’s validity.
Impact on Deliverability
SPF’s impact on deliverability is significant. By authenticating your domain, it:
- Reduces the likelihood of emails being marked as spam.
- Enhances the sender’s reputation, which ISPs favor.
- Improves email delivery rates significantly.
This deepens our understanding of Email Authentication for Better Deliverability, emphasizing SPF’s critical role.
DKIM: A Key to Email Authentication for Better Deliverability
How DKIM Works
DKIM stands as a beacon of integrity in the world of email security. Imagine it as a digital fingerprint, unique to each email, ensuring the message remains untampered from sender to receiver. This cryptographic approach combines a public key, published in your DNS records, with a private one, securely held on your mail server. By securing email content, DKIM becomes an indispensable tool for Email Authentication for Better Deliverability.
Steps for Setting Up DKIM
- Generate Your DKIM Key: Start by creating a DKIM key pair – one public, one private.
- Publish the Public Key: Add it to your DNS records, making it visible to email recipients.
- Configure Your Email System: Ensure it signs outgoing emails with your private key.
Role in Email Security
In our quest for better deliverability, DKIM plays a crucial role. It’s not just about keeping spam at bay; it’s about building trust. When receivers see that an email is DKIM-signed, it’s like a seal of authenticity, dramatically boosting sender reputation and reducing the likelihood of being blacklisted.
Engage with DKIM: Dive into its mechanics and embrace its security prowess. By implementing DKIM, you’re not just enhancing security; you’re fortifying your position in the digital communication landscape. After understanding the basics of DKIM, you might want to dive deeper into its setup process. For comprehensive steps, check out these comprehensive DKIM implementation steps.
DMARC’s Role in Email Authentication for Better Deliverability
Understanding DMARC
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is pivotal in Email Authentication for Better Deliverability. It’s akin to a digital sentinel, ensuring emails genuinely represent your domain.
Implementation Strategies
To effectively implement DMARC:
| Step | Description |
|---|---|
| 1. Identify Email Sources | Determine where your emails are sent from. |
| 2. Create a DMARC Record | Add a line of text to your DNS record. |
| 3. Choose a Policy | Start with ‘none’, then progress to ‘quarantine’ or ‘reject’. |
Benefits for Email Deliverability
DMARC enhances deliverability through:
- Improved Trust: Elevates sender reputation to combat spam traps and blacklisting.
- Enhanced Security: Works alongside SPF and DKIM for layered protection.
- Visibility: Offers insights on email performance and origins.
🛡️ DMARC: Your Digital Email Guardian – A vital tool for ensuring your brand’s credibility and security in the online world.
Integrating DMARC is not just a tactic; it’s a strategic move to fortify your brand’s digital trust and security. Essential in the realm of Email Authentication for Better Deliverability, DMARC is a non-negotiable element of a robust email strategy.
Building a Robust Email Authentication Strategy
Integrating SPF, DKIM, and DMARC
In the quest for Email Authentication for Better Deliverability, integrating SPF, DKIM, and DMARC stands paramount. Think of it as assembling a security trifecta. Each protocol adds a layer of trust and verification, crucial in the fight against email spoofing and phishing.
- SPF (Sender Policy Framework): Validates emails from your domain.
- DKIM (DomainKeys Identified Mail): Ensures the content remains tamper-free.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): Aligns SPF and DKIM for a cohesive security posture.
Best Practices for Optimal Setup
Key Steps:
- Consistent Implementation: Ensure all three protocols are uniformly configured across your email channels.
- Regular Updates: Keep your SPF records and DKIM keys up-to-date.
- Monitoring and Reporting: Utilize DMARC reporting to track authentication successes and failures.
Common Pitfalls and Solutions
Common Email Authentication Challenges
| Challenge | Solution |
|---|---|
| SPF Record Overload | Simplify by consolidating senders |
| DKIM Signature Failures | Regularly check key lengths and settings |
| Misconfigured DMARC | Start with a ‘p=none’ policy and gradually enforce |
Remember: Overlooking these protocols can lead to higher bounce rates and poor sender reputation. Regularly auditing your setup can save you from falling into spam traps and blacklists.

Advanced Email Authentication Techniques
Emerging Trends in Email Security
In the fast-paced world of digital communication, email security is evolving rapidly. Next-generation technologies are reshaping how we protect our inboxes. From AI-driven filters to behavioral analysis, the landscape is witnessing a tech revolution. Did you know AI can now predict and thwart potential email threats before they hit your inbox?
Next-Gen Authentication Methods
The rise of Blockchain in Email Authentication is a game-changer. It adds an unbreakable layer of verification, ensuring the authenticity of each email. Imagine emails backed by blockchain – the ultimate shield against phishing!
Machine Learning (ML) isn’t far behind. It’s fine-tuning SPF, DKIM, and DMARC protocols, making them smarter and more adaptive to new threats.
Interactive Email Security: It’s not just about detecting threats anymore. It’s about engaging users in security practices. Interactive authentication methods are becoming popular, making users active participants in their email security.
Cutting-edge Email Authentication Technologies
| Technology | Description |
|---|---|
| AI and ML | Enhancing existing protocols with predictive capabilities |
| Blockchain | Providing a tamper-proof authentication system |
| Interactive Security | Engaging users in the security process |
Email Authentication for Better Deliverability is no longer a choice; it’s a necessity. With cyber threats lurking around every corner, these advanced techniques are our digital knights in shining armor.
Remember, the key to effective email security is staying ahead of the curve. Embrace these trends, and watch your sender reputation soar while bounce rates plummet!
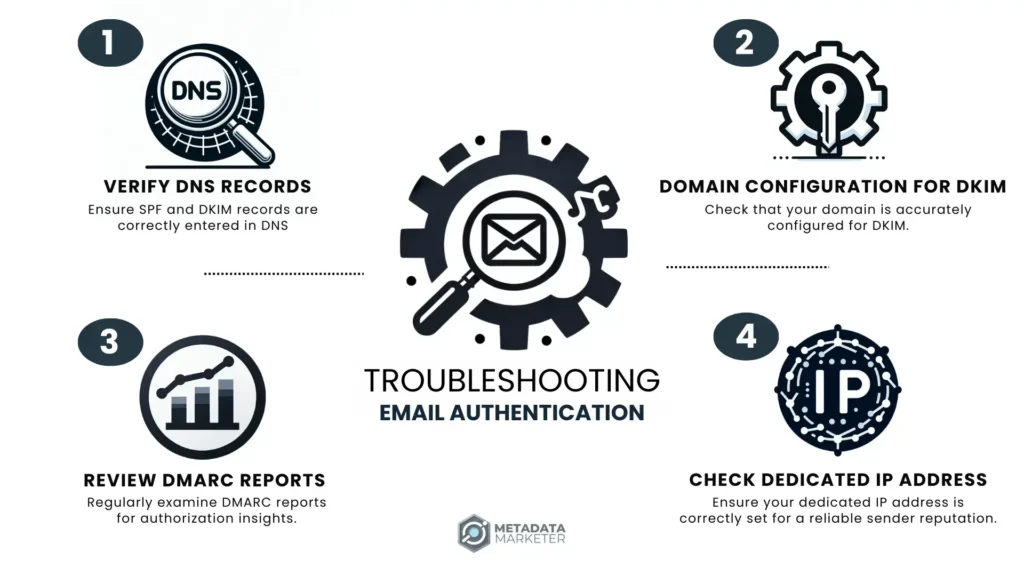
Troubleshooting Common Email Authentication Issues
Resolving Typical Setup Problems
Encountering challenges during Email Authentication setup is common. Effectively addressing these issues is crucial for ensuring Email Authentication for Better Deliverability. Let’s unravel these mysteries:
- Firstly, check your DNS records. Incorrect entries often derail SPF and DKIM setup.
- Secondly, verify your domain’s configuration. A misconfigured domain can lead to failed DKIM signatures.
Handling Altered Messages and Authorization Challenges
Altered messages and authorization woes? No worries! Here’s how to handle them:
- Altered Messages: Ensure your DKIM signatures align precisely. Mismatched signatures are a common culprit.
- Authorization Challenges: Regularly review your DMARC reports. They provide invaluable insights into potential authorization issues.
Pro Tip: Use a dedicated IP address for better control over your sender reputation.
Quick Checklist:
- DNS Records: Correct and verified?
- Domain Configuration: Accurately set up for DKIM?
- DMARC Reports: Regularly checked for insights?
Impact of Email Authentication on Marketing Campaigns
Enhancing Marketing Email Deliverability
In the pursuit of impeccable deliverability, Email Authentication stands as a critical asset for marketing strategies, transcending the mere avoidance of spam folders to genuinely earning customer trust. With the implementation of SPF, DKIM, and DMARC, emails are not just sent; they are delivered with a seal of authenticity.
Case Studies: ROI and Engagement Improvement
- PayPal saw a significant reduction in email spoofing and phishing, safeguarding both their users and the organization, by deploying DMARC, DKIM, and SPF policies.
- LinkedIn implemented these email authentication standards to enhance the security of its email communications and protect its domain from fraudulent emails.
- Bank of America adopted DMARC and shifted their policy to “quarantine” to protect customers from phishing and spoofing, demonstrating the protocol’s efficacy in enhancing email security.
Email Authentication Impact on ROI
These case studies illustrate the tangible benefits of Email Authentication for Better Deliverability in marketing campaigns, showcasing a direct correlation between enhanced security protocols and improved trust and engagement with customers.
Remember: A well-authenticated email is your ticket to not just a viewer’s inbox but to their trust—paving the way for a successful digital marketing journey.
Legal and Compliance in Email Authentication
Adhering to Email Laws and Regulations
In the quest for Email Authentication for Better Deliverability, it’s imperative to navigate the intricate web of email laws and regulations. Compliance isn’t just about following rules; it’s a commitment to maintaining trust and integrity in digital communication.
- Global Email Compliance Laws: Stay updated with evolving laws like GDPR in Europe, CAN-SPAM in the US, and CASL in Canada. Each region has its nuances, demanding tailored strategies for compliance.
- Data Protection and Privacy: The key to legal compliance is respecting user data. Implementing SPF, DKIM, and DMARC goes a long way in safeguarding data integrity.
Global Compliance Best Practices
Global compliance is a jigsaw puzzle, but here are some best practices to fit the pieces together:
- Regular Audits: Conduct regular reviews of your email authentication practices. Ensure your SPF and DKIM records are up-to-date.
- Consent and Transparency: Always obtain explicit consent for email communication. Be transparent about your data use policies.
- Stay Informed: Email laws are dynamic. Keep abreast of changes and adapt your practices accordingly.

For the latest cybersecurity directives and updates, visit Cybersecurity Directives on the official CISA website.
Case Studies: Success Stories in Email Authentication
Real-world Examples
E-commerce Giant Boosts Revenue with Clean Inbox:
- Challenge: High bounce rates, emails in spam.
- Solution: Implemented DMARC, SPF, DKIM.
- Results: Deliverability was up by 35%, open rates increased by 20%, and revenue was up by 15%.
Business Communication Impact
Nonprofit Builds Donor Trust with Secure Communication:
- Challenge: Struggled to engage donors over email security concerns.
- Solution: Adopted email authentication, and emphasized data privacy.
- Results: 28% rise in donations, increased donor trust.
Travel Agency Enhances Customer Experience with Reliable Delivery:
- Challenge: Booking confirmations and updates landing in spam.
- Solution: Integrated email authentication.
- Results: 40% increase in deliverability, reduced support tickets, and improved customer satisfaction.
Financial Services Provider Safeguards Sensitive Information:
- Challenge: Vulnerable to spoofing, and potential security risks.
- Solution: Enforced strict email authentication, and phishing awareness.
- Results: 95% reduction in spoofing incidents, enhanced regulatory compliance, bolstered brand image.
Key Takeaways:
- Increased Revenue: Direct link between improved deliverability and higher revenue.
- Brand Reputation: Secure emails foster trust and loyalty.
- Risk Reduction: Authentication protects sensitive data and ensures compliance.
- Customer Experience: Reliable email delivery enhances overall customer satisfaction.
These case studies demonstrate that Email Authentication for Better Deliverability is not just a technical necessity but a strategic asset for varied industries, impacting everything from revenue to customer trust.
Conclusion and Future Outlook
Key Takeaways
In our journey through Email Authentication for Better Deliverability, we’ve uncovered the transformative power of SPF, DKIM, and DMARC in securing digital communication. These protocols are not just tools; they are guardians of sender reputation and email engagement, mitigating spam traps and blacklist risks.
- SPF: Validates email sources, enhancing trust.
- DKIM: Ensures email content remains untampered.
- DMARC: Aligns SPF and DKIM for holistic protection.
Trends and Future Directions in Email Authentication
Looking ahead, email authentication is poised for exciting advancements:
- AI-Driven Security: Incorporating artificial intelligence for predictive threat detection.
- Advanced TLS Encryption: Strengthening email privacy.
- Dedicated IP Strategy: Tailoring IP usage for specific sender needs.
🔍 Did You Know?
The integration of AI in email security is set to revolutionize how we perceive email deliverability.
As I conclude my discussion of email authentication techniques, it’s important to emphasize that these protocols are vital for securing your email communication. However, if you’re curious about the practical applications of these techniques within email marketing platforms, you’ll find valuable insights in my detailed comparison of Moosend vs TinyEmail. This section provides insights into how these platforms implement email authentication and the benefits they offer.
Frequently Asked Questions
How to implement DMARC for better email security?
This is a great question, as DMARC is a powerful tool for protecting your domain from spoofing and phishing. Implementing it can be a bit technical, but there are plenty of resources available to help you get started.
Here’s a simplified overview:
1. Set up SPF and DKIM: These protocols verify that emails coming from your domain are actually authorized by you. Think of them as like a digital passport for your email.
2. Publish a DMARC record: This record tells email providers what to do if an email fails authentication. You can choose to quarantine suspicious emails, reject them outright, or just monitor the situation.
How does SPF improve email deliverability?
SPF helps email providers trust your emails and less likely to send them to spam. It works by listing all the authorized IP addresses that can send emails on your behalf. This way, spammers can’t just forge your email address and have their messages sail through.
What is email authentication?
Email authentication is a set of protocols that help verify the sender of an email. It’s like showing your ID when you’re trying to get into a club – it proves you’re who you say you are. This is important because it helps prevent spammers and phishers from impersonating legitimate businesses or individuals.
Why is email authentication important for business communication?
Email authentication is crucial for businesses for many reasons:
– Protects your brand reputation: Spoofed emails can damage your brand image and customer trust. Authentication helps prevent this.
– Improves email deliverability: Emails from authenticated senders are less likely to be flagged as spam, ensuring your messages reach your intended audience.
– Compliance: Some regulations require businesses to use email authentication.
What are the benefits of email authentication for marketing?
Email authentication offers several benefits for email marketing:
– Higher open rates: People are more likely to open emails from trusted senders.
– Increased engagement: Authenticated emails are less likely to end up in the spam folder, leading to more clicks and conversions.
– Improved sender reputation: A good sender reputation can lead to better placement in inboxes and higher campaign performance.
How can email authentication reduce spam?
Email authentication makes it harder for spammers to spoof legitimate email addresses. This is because spammers typically don’t have access to the required authentication keys and records. By verifying the sender, email providers can significantly reduce the amount of spam that reaches inboxes.
How does email authentication impact sender reputation?
Email authentication plays a major role in sender reputation. When you consistently send authenticated emails, your reputation improves, leading to better deliverability and inbox placement. Conversely, if your emails fail authentication, your reputation can suffer, and your emails might be sent to spam.
What are common issues with email authentication setup?
Setting up email authentication can sometimes be tricky.
Here are some common issues:
– DNS configuration errors: Make sure your SPF, DKIM, and DMARC records are properly configured in your DNS zone.
– Missing or outdated keys: Keep your authentication keys up-to-date and ensure they’re not shared publicly.
– Inconsistent sender information: Always use the same domain name and email address throughout your email sending process.
By understanding these potential issues and taking steps to avoid them, you can ensure a smooth email authentication setup and reap all its benefits.

